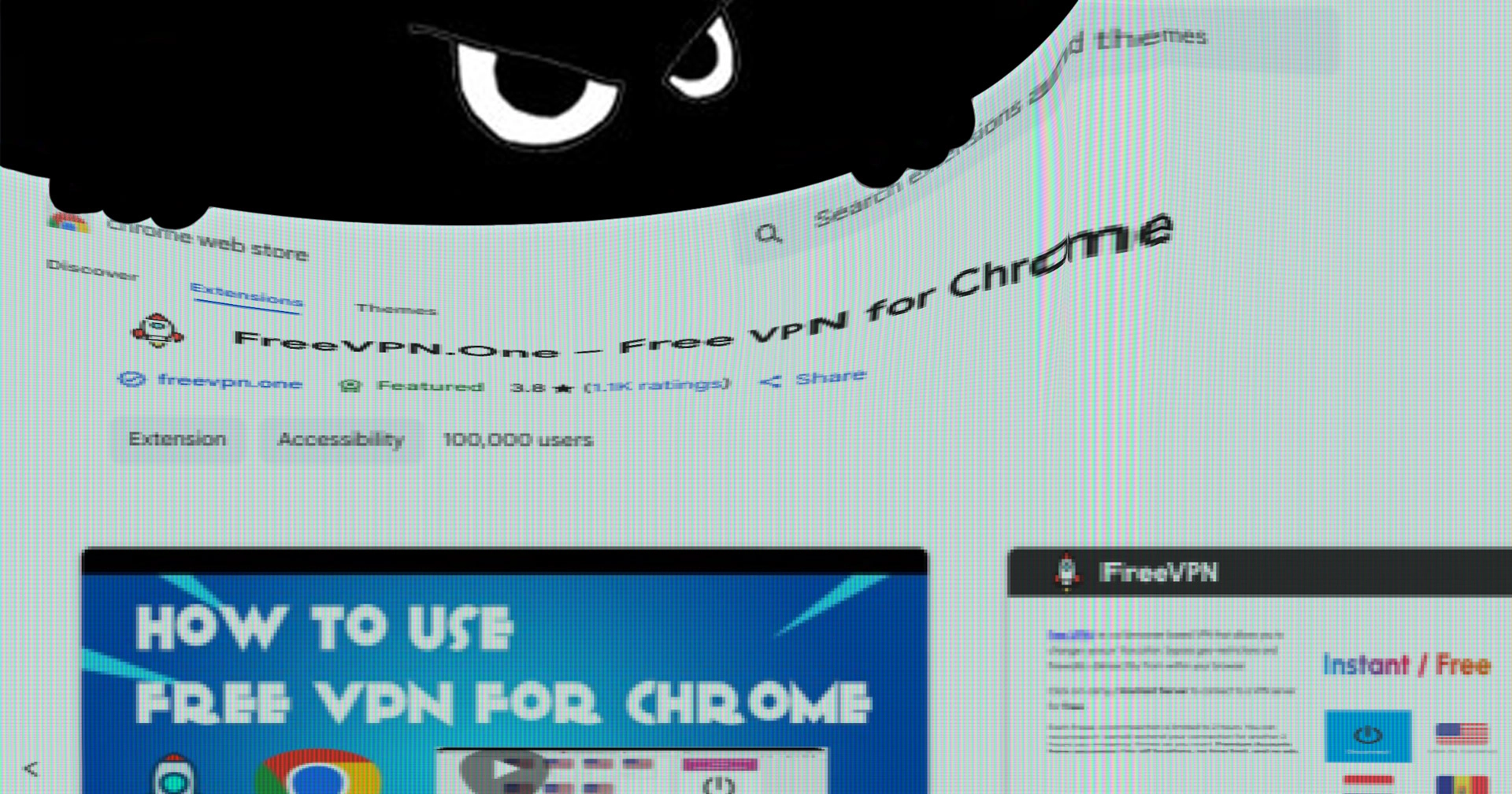
If you are a user of Google Chrome or any Chromium-based browser and have installed a free VPN extension from the Chrome Web Store, it’s vital to verify its legitimacy. This caution is especially crucial for users in the UK, where VPN usage has surged recently due to the implementation of online age verification systems.
Not all VPN services are created equally—some are fundamentally exploitative. A free VPN extension reviewed by Koi Security, initially appearing trustworthy, was discovered to be spying on users extensively instead of providing protection. Researchers noted the extension’s real purpose was to monitor activities rather than secure users’ privacy.
The extension began as a basic VPN but underwent significant changes in 2025, progressively gaining increased permissions under the guise of enhancing user security:
- In April, it requested permission for
<all_urls>, allowing access to every website visited. - By June, it gained scripting permissions.
- In July, it began capturing screenshots and collecting location and device information, ultimately encrypting this data to avoid detection.
After a webpage loads, content scripts activate after a brief delay, capturing screenshots using Chrome’s privileged API. This surveillance could compromise sensitive information, including financial data, personal communications, and more—without the users’ informed consent.
The extension cleverly marketed a component called "AI Threat Detector" that claimed to analyze websites for potential phishing threats. This feature, however, masked the continuous monitoring that users were unknowingly subjected to. Many users trust these tools thinking they are engaging with a one-time security check, rather than persistent oversight of their online activities.
Despite these alarming revelations, the extension has over 100,000 installs and continues to be available on the Chrome Web Store, still featuring Google’s promotional badge. Less tech-savvy users may overlook the risks, underlining a troubling reality: if a product is free, the users are often the product.
For further insights, you can read the full Koi Security blog post detailing how these events unfolded and why Google’s oversight failed to detect these activities.